As web application security has been increasingly relevant recently, we decided to release the next part of the article on the top 5 web attacks we published earlier last year. In this part, Yuriy Myrosh, Head of JavaScript Development at LS, reviews some other widespread web threats business owners should look out for.
The article determines the most critical vulnerabilities and explains how to avoid them. Keep reading to check whether your software is protected against malware and determine which measures will help you stay safe.
Why protecting software against different types of web attacks matters?
Web attacks can not only entail financial expenses but also lead to losing your clients and damaging your business reputation. Among some large-scale web attacks are botnets, like Mirai, settings misconfiguration, sensitive information exposure, etc.
One of the massive DDoS attacks performed with the Mirai botnet assaulted around 145K devices and disabled Twitter, Reddit, Netflix, and other large-scale websites. Settings misconfiguration in Jira exposed sensitive data about NASA project details and employee internal information, which was another case of improper security management. Facebook also faced issues with personal data leakage that resulted in 600 million users' account information exposure.
The extent of security failures is impressive, making each business owner consider ways to avoid them. We decided to help business owners navigate the security topic more easily and prevent security vulnerabilities. This article reviews cryptographic failures, insecure design, security misconfiguration, software and data integrity failures, and server-side request forgery in detail.
1. Cryptographic failures
This type of web attack was previously referred to as sensitive data exposure. It implies system compromises related to cryptography — concerns associated with algorithms and their implementation.
Any personal information like user credentials, passwords, credit card details, and health records requires adequate protection to prevent such breaches. You also should consider privacy laws relevant to your location, like the EU's General Data Protection Regulation (GDPR) or US' California Consumer Privacy Act (CCPA). Regulations include guidelines that should help avoid cryptographic failures in your software.
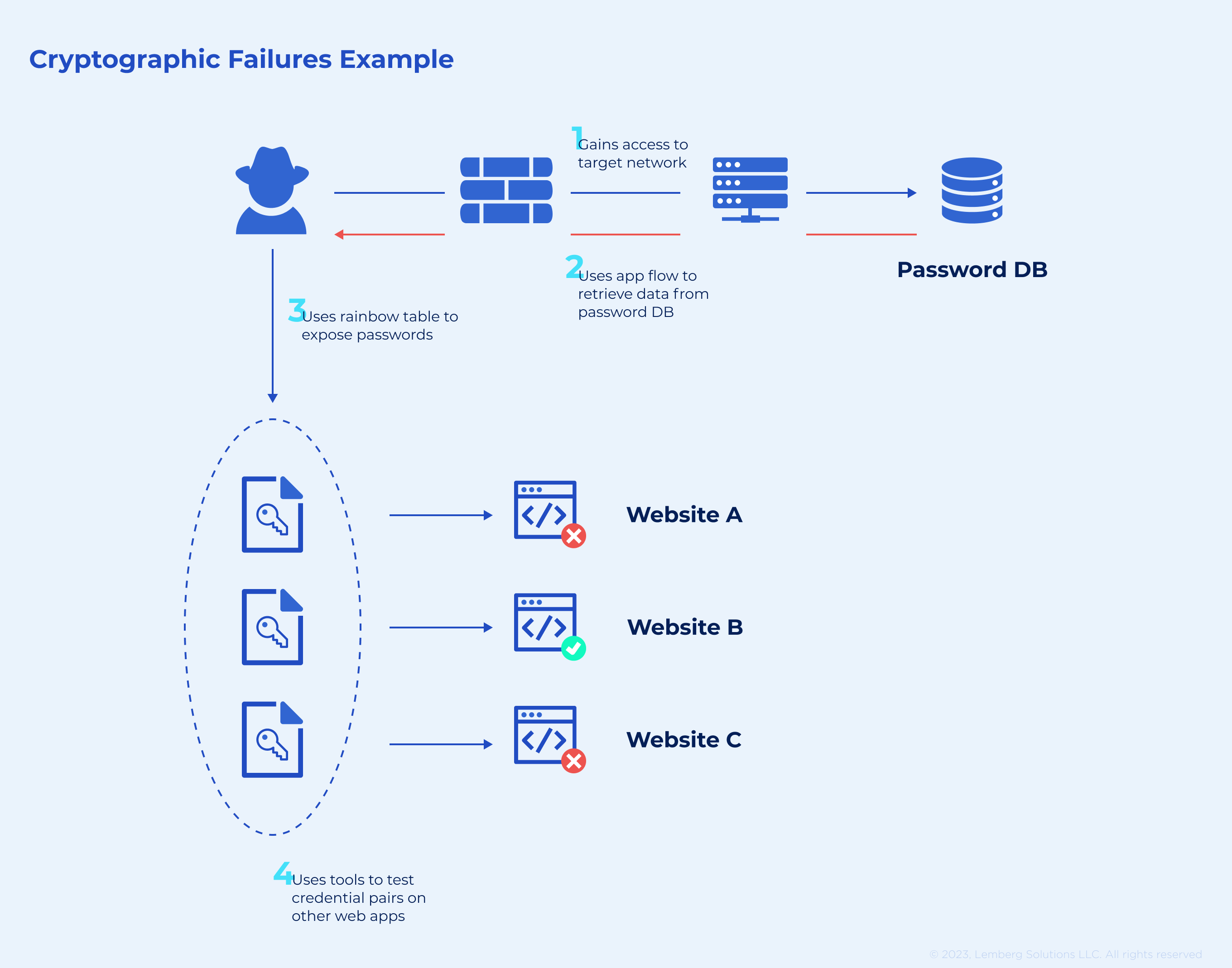
If you want to avoid this web threat, check out the most widespread cryptographic vulnerabilities below and stay alert:
- Unauthorized internet traffic between web servers could provoke a web attack. Thus, internal traffic must comply with HTTP, SMTP, and FTP protocols
- Outdated algorithms and protocols in legacy code
- Generating keys that don't meet security standards or missing proper key management in source code repositories might also lead to cryptographic web app attacks
- Invalid server certification and issues with the trust chain
- Insufficient security of initialization vectors and inappropriate encryption mode
- Lack of true randomness (entropy) used for higher cryptography security (pseudo-random cryptography)
- Using non-cryptographic hash functions
- Utilizing PKCS number 1 v1.5 or other outdated cryptographic padding methods
- Ineffective configuration and settings.
Noticed some of the enlisted vulnerabilities in your processes? Don't hesitate to contact a security expert to find out whether your business is under threat of data breaches and how to prevent them.

How to prevent cryptographic failures?
We decided to compile an actionable list on how to avoid cryptographic failures. Follow this advice to prevent cryptographic-based web attacks for your business:
- Structure and classify the data you process and store, making sure it is appropriately managed based on relevant laws and requirements
- Delete unnecessary data as soon as you can for theft prevention
- Encrypt data using TLS, HTTP Strict Transport Security (HSTS), and authenticated encryption. Avoid using free self-signed certificate authority providers
- Manage keys properly, using up-to-date algorithms and protocols
- Avoid FTP, SMTP, and other outdated protocols for transferring sensitive data
- Use hash functions to keep strong passwords, e.g., Argon2, scrypt, bcrypt, or PBKDF2
- Opt for appropriate initialization vectors according to the specific operation mode (CSPRNG)
- Generate random keys and store them at byte arrays. Make sure to use cryptographic randomness
- Avoid MD5, SHA1, PKCS number 1 v1.5 and other legacy functions.
Paying attention to cryptographic weaknesses can prevent sensitive information breaches and save you from losing your business reputation. Mind that an experienced security team can help you manage this process more efficiently.
2. Insecure design
This web vulnerability relates to every design-related risk you could come across. Insufficient business risk profiling in the system under development is the main reason for design insecurities. It can also occur due to failure to define the correct level of design security required.
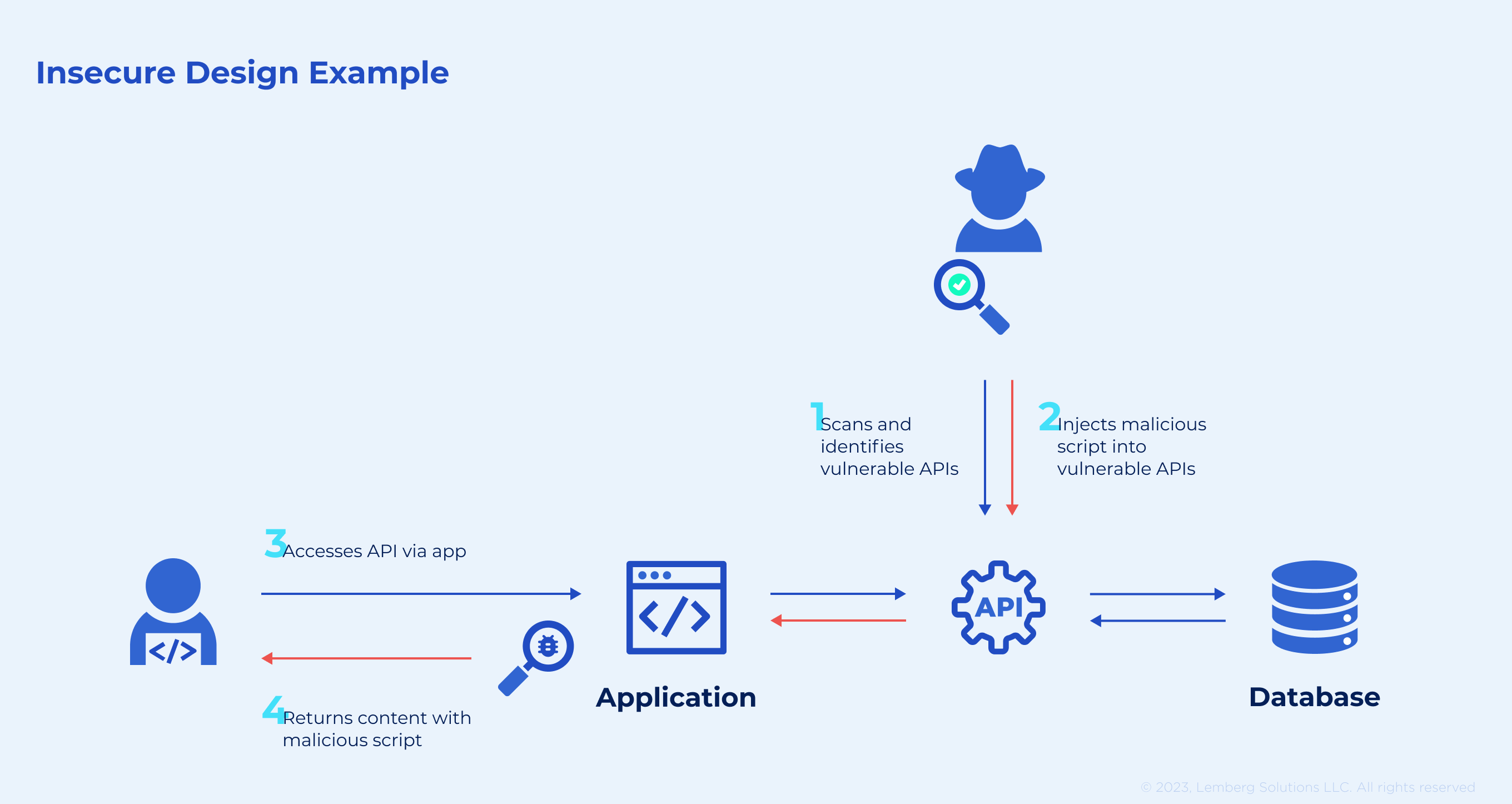
Three must-have values of a secure design
Secure design has three core features — optimal resource management, secure design, and secure development lifecycle. Let's review each of these values in more detail:
How to structure an optimal resource management
Structure tech requirements and discuss design, build, testing, operation, and security costs. Business requirements should be collected in advance, considering the expected confidentiality of the data involved. Apart from this, think about application exposure to properly manage access control.
How to create a secure design
Secure design is a complex of activities intended to effectively prevent web security attacks. Threat management is one of the critical principles of secure design. While creating user stories, you must define the proper flow and failure states. Build, test, and validate assumptions to create reliable failure flows. Document your results in user stories.
How to build a secure development lifecycle
Plan a secure development lifecycle from the beginning of the software development process. For this, you can use consulting on web development services of a reliable vendor or engage security professionals.
How to prevent insecure design?
Insecure design can impact a wide range of processes within your company, which means preventing this threat is crucial for your business. Here's the list of actions that will help you build processes effectively without putting your procedures under any risks:
- Utilize secure design patterns or ready-to-go components
- Make sure you have a reliable threat management procedure for critical authentication, access control, and business logic
- Compile user stories with security language and controls
- Set up plausibility checks for both the front and back ends of your software
- Make sure that your procedures are resistant to malicious code via writing detailed unit and integration tests; compose use-cases and misuse-cases
- Separate system layers based on the exposure and security needs
- Restrict consumption of resources.
Check out whether your product development procedures comply with the described recommendations. In case there are some gaps in your processes, consult a reliable security partner.
3. Security misconfiguration
Inaccurate configuration of your security controls can risk the whole system and data. Security misconfiguration can occur for several reasons like poor documentation, default settings, or technical issues with components.
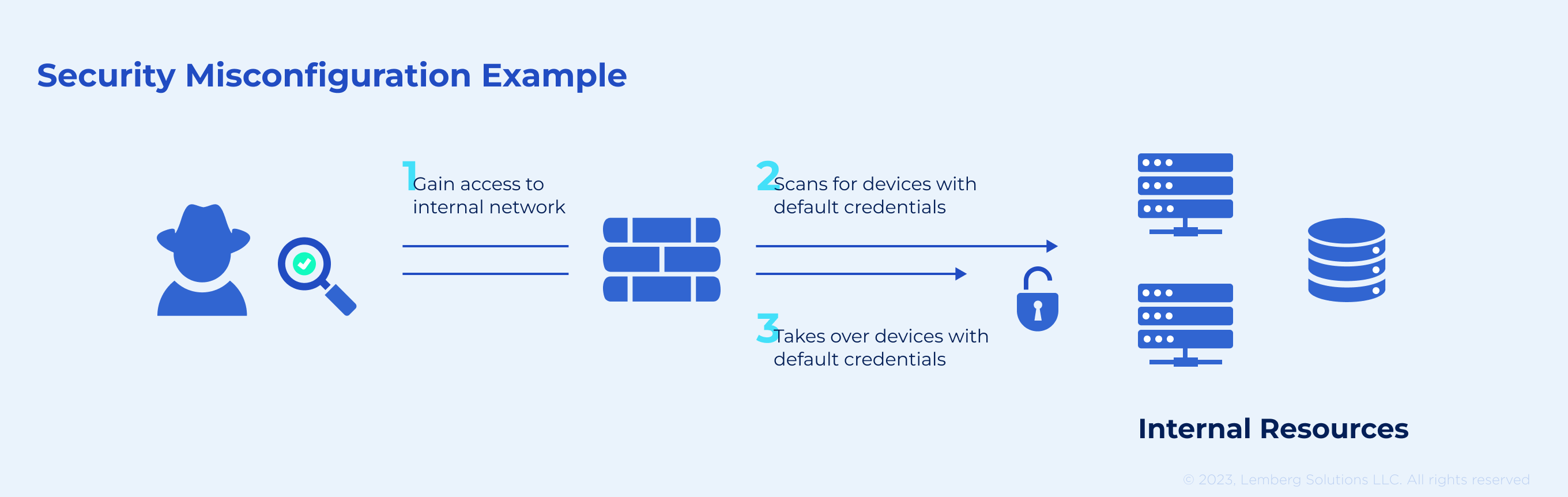
Your security is misconfigured if:
- The software is missing configured permissions and lacks proper security hardening
- Excessive features are enabled
- The system uses default credentials and accounts
- Users receive overly detailed error messages with stack traces
- Upgraded security features aren't used/configured
- Security settings of servers, frameworks, and databases are missing secure values
- Security headers and directives aren't set and sent by the server
- Your software is composed of vulnerable components and is out of date
- You're missing a regulated app security configuration process.
Explore your security configuration based on the above points and learn whether your business is secured against internal resources breaches.
How to prevent security misconfiguration?
Let's review some insights on how to save your business from security misconfiguration:
- Restrict access by default and provide rights only to necessary resources
- Set up a repeatable security hardening process and ensure that each environment, including development, quality assurance, and production, is configured in the same way. Mind that each different environment requires unique credentials
- Delete unnecessary features and frameworks to ensure your platform doesn't contain excessive components and documentation
- Set up a patch management process to review and update relevant configurations
- Ensure your application architecture is segmented appropriately
- Send security directives to your clients
- Automate your verification processes to check the settings and configurations in each environment.
Follow these tips to prevent security misconfiguration. If you need any help with software development security, contact us.
4. Software and data integrity failures
Code and infrastructure that aren't secured against integrity violations can lead to software and data integrity failures. Using untrusted sources and insecure CI/CD pipelines are examples of poor system protection. Automated updates might be another threat. Without a thorough analysis, cyber criminals can easily distribute malicious software across your system disguised as a regular update.
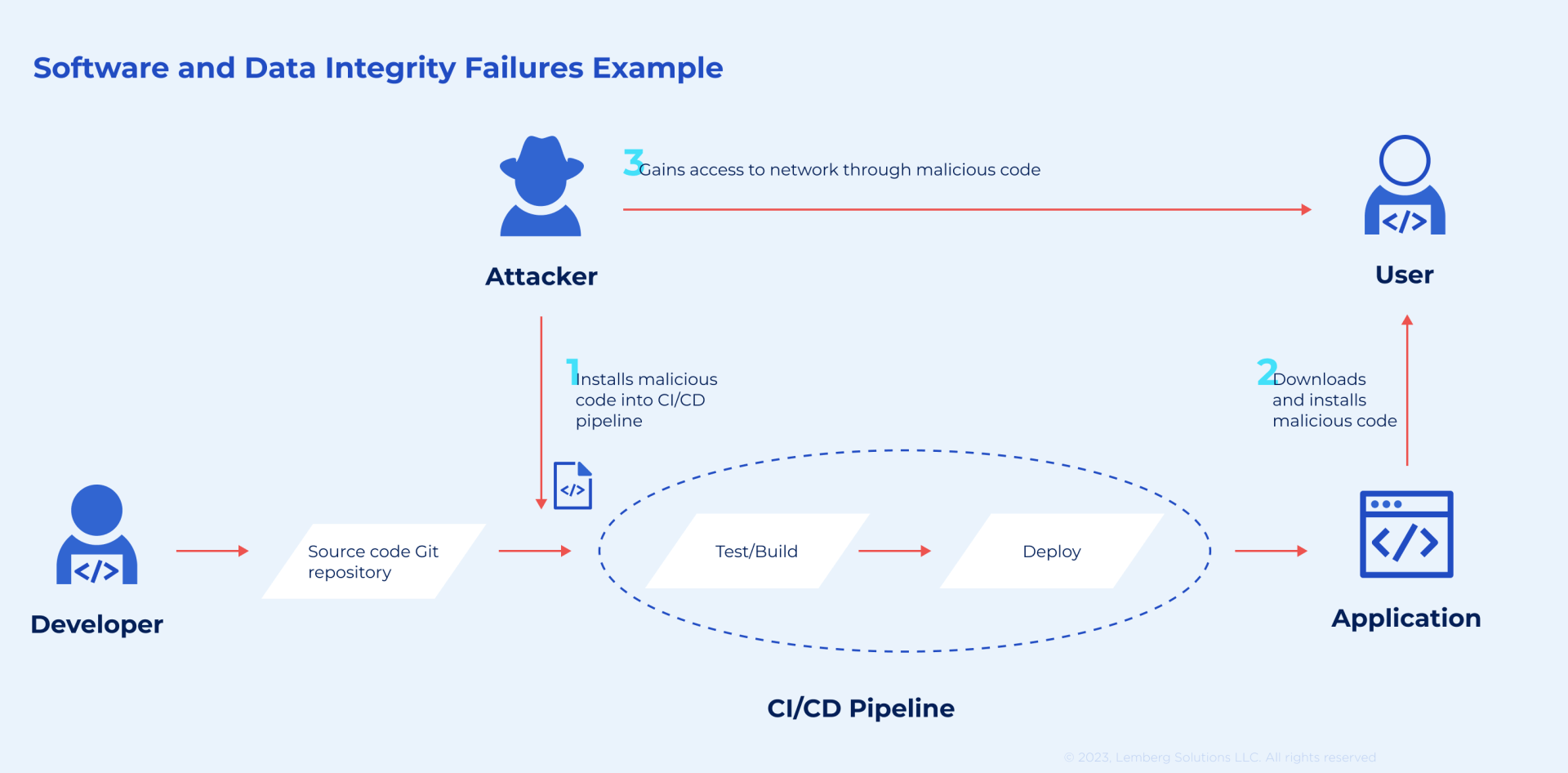
How to prevent software and data integrity failures?
Make sure your business is secured against data integrity failures by following these tips:
- Check the reliability of data sources by using digital signatures
- Use only trusted repositories. In case you have a higher risk profile, utilize an internal repository
- Adopt OWASP Dependency Check, OWASP CycloneDX, or another supply chain security tool to eliminate potential weaknesses
- Establish a code-review process to make sure your software pipeline is free from malicious code/configurations
- Ensure that build and deploy processes use integral software with appropriate configuration and access control
- Avoid sending serialized data that isn't encrypted/signed to untrusted clients before running some integrity verification or digital signature.
Malicious code can lead your system to severe breakdowns and considerable losses. So you should take secuirty precautions at every development stage.
5. Server-side request forgery
Complex architectures and cloud services increase the risk of SSRF attacks. Omitting URL validation while fetching a resource can cause a server-side request forgery. In this case, software hackers can forward requests from your application to an unknown destination. Even ACLs (network access control list) won’t stop them.
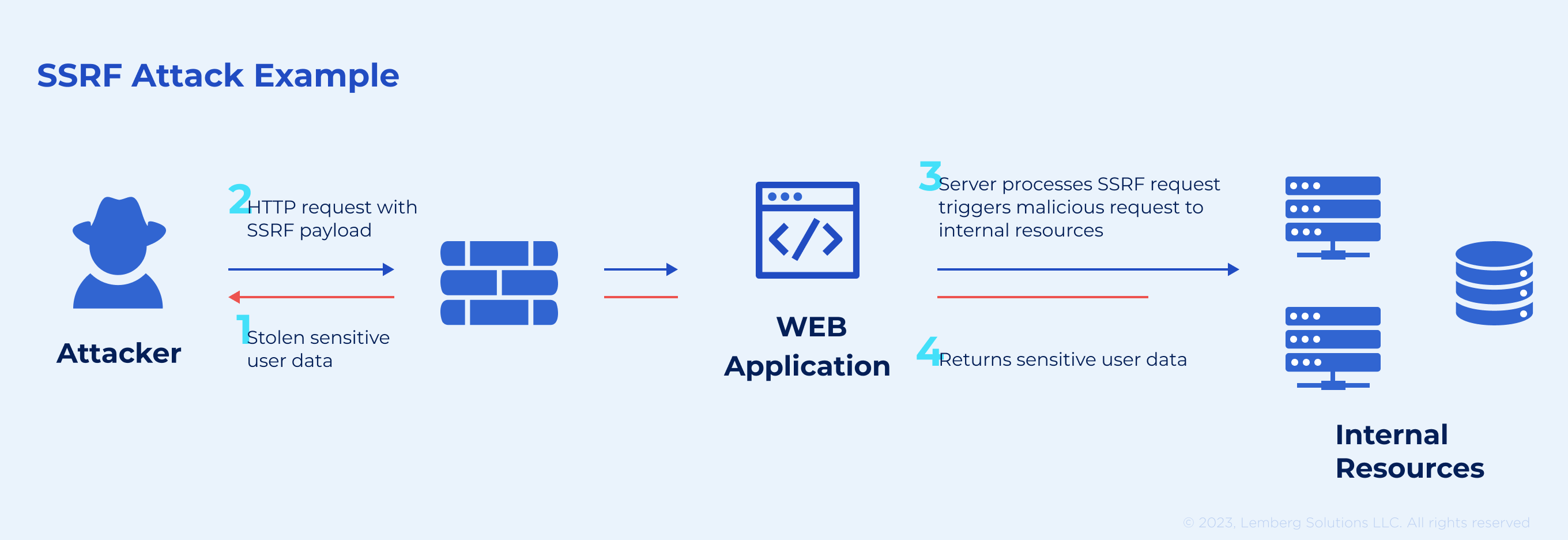
How to prevent server-side request forgery?
You can address SSRFs from different angles — network layer, application layer, and other measures. Let's review each of them in more detail below:
Network layer:
- Classify remote resource access into separate networks
- Set up network access control rules to limit unnecessary intranet traffic
- Manage firewall rules and log all network flows.
Application layer:
- Verify input data from your clients
- Introduce URL schema
- Send processed responses to users
- Deactivate HTTP redirects
- Keep in mind URL consistency.
Additional measures to consider:
- If you need to meet high-security needs, use network encryption
- Don't use other security providers on front systems (e.g., OpenID). Instead, control local traffic with systems like localhost.
Check whether your system meets the security requirements to prevent SSRF. Contact us to learn more about this vulnerability and how to avoid it.
Final thoughts
After reviewing different types of web attacks, it becomes clear that introducing web security features into your system is essential. Whether you're a small business owner or manager of an international corporation, there's no guarantee against cyber attacks except for continuous work on security measures.
If you're looking for software development and security policies consulting, contact us, and we'll get back to you shortly. We build every app with top security practices in mind.




