The very idea of mesh networks is not new. LoRaWAN, Zigbee, and WiFi mesh networks are already used for various IoT cases. Bluetooth Mesh differs since it is mostly used for the automation of buildings that allows to transmit data wirelessly. Its network offers a reliable connection for large-scale projects. Up to 32 thousands of wireless devices can communicate with each other without being tied to a central hub.
With such a wide coverage, BLE mesh networking can be used for:
- Home automation
- Smart lighting
- Electric smart meters
Our developers' IoT development services expertise allows us to discuss all of the above aspects in detail. We prepared a 5-steps demo on how to create a Bluetooth Mesh network of smoke detectors and therefore reimagine the safety measures of your building. Continue reading to learn more.

How does Bluetooth Mesh work?
Bluetooth mesh is a networking protocol based on Bluetooth Low Energy. As if in a spider’s web, Bluetooth mesh follows the rules of many-to-many communication. This networking protocol does not require a central hub. The devices are all interconnected (or at least many of them with many others). But let us first have a look at what makes a device a node.
New device provisioning
After a device joins the mesh network it is called a node. The process of joining is known as node provisioning and the device that adds other devices is a provisioner.
The provisioning process consists of five stages:
- Beaconing
During the first stage, BLE advertising functionality searches for a not connected device that indicates its availability. - Invitation
Once the unprovisioned device is found, the provisioner sends an Provisioning Invite PDU and the device sends a Provisioning Capabilities Packet, a collection of information about the device. - Exchanging Public Key
The provisioner and the device to be provisioned exchange their Public Keys to make the connection perfectly secure. They may use both the BLE channel and out-of-band (OBB) channel. - Authentication
One more step towards the security confirmation is the stage of authentication. The device to be provisioned enters a random number or a static passkey to the provisioner, and then they check the confirmation value. - Provisioning data distribution
Once the authentication is complete, the provisioner and the unprovisioned device exchange a session key, a device key, and a unicast address.
Hey presto! Your device is now a node on the BLE mesh network. Let’s move on how the nodes communicate.
Node communication
The interconnection of nodes occurs with the help of message-oriented communication - a managed flood process. Managed flood ensures a multipath approach to data transition that guarantees a message meets its destination. Even if one node fails, the data will be automatically redirected over a different path, securing data transition.
Bluetooth mesh implements a publish/subscribe communication approach. It guarantees that different types of devices can coexist within a network without being bothered by messages from other unsubscribed devices. The process of publishing relies on sending messages to addresses whose names and definitions correlate with high-level principles that users may recognize. And under the term subscribing, devices may be programmed to accept messages which certain devices have sent to specific addresses.
Nodes transport data via either of two protocol stacks, the Advertising bearer or the GATT bearer. Advertising bearer receives and transmits messages from and to other nodes and GATT bearer is responsible for the communication between the devices that don’t support the advertising bearer and ones that do.
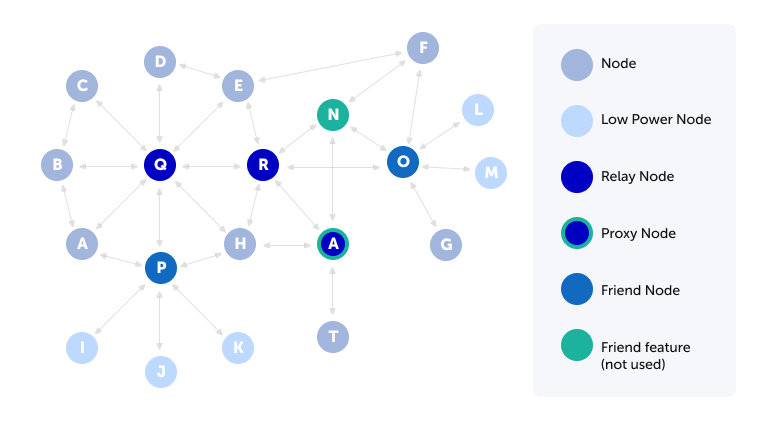
Node topology
Each node can be classified according to the features it performs:
- Low Power and Friend nodes. Low Power is a useful type of node for the devices that operate on batteries, since Low Power nodes do not need to listen for the incoming messages continuously. From time to time, it pings a Friend node to check for any pending messages. After the check, it goes back to its regular low-power mode.
- Relay node is operating with the ability to retransmit received messages.
- Nodes that support Proxy feature are the entry point into the Mesh network for those devices that don’t directly support Bluetooth Mesh, since it allows devices, such as a smartphone or a Wi-Fi-Bluetooth Mesh gateway, to communicate with the Mesh network.
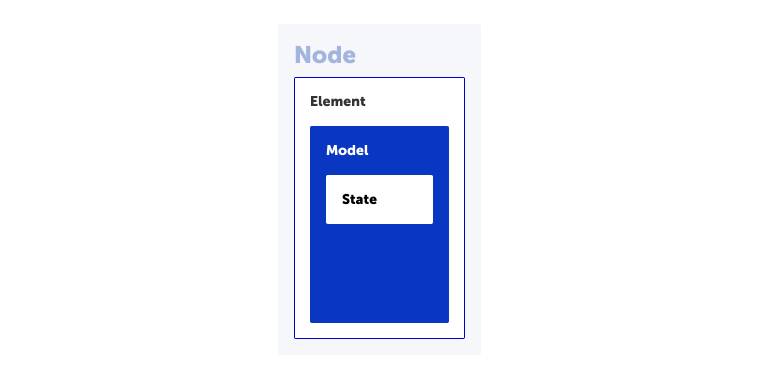
BLE node structure
To function as a BLE mesh device, one node must have at least one element. In turn, one element must possess at least one model. The model gives the understanding what functions have a node. And the possible conditions of the function are defined in the model state.
For example, a smoke detector that will be used in our demo, has one function and several states:
- Node = Smoke Detector
- One Element = Primary Element
- Functionality of node
1. True/False - Condition/State of Element
1. True or False
There are three types of models:
- Client - sends messages to the server model
- Server - has a state and responds to the Client model requests
- Control - implements both client and server features; may include control logic, which specifies the rules for coordinating interactions between the control model and other client and server models.
Smoke detectors network demo
The goal of this demo is to create a Bluetooth Mesh network of smoke detectors in five steps. The sensors would be able to easily integrate into both new and existing Bluetooth Mesh networks. After provisioning, you can collect data from the network using a smartphone application.
1. Selecting hardware components
The main component of the device will be a microcontroller. It will be responsible for Bluetooth Mesh communication and the processing of the smoke detector data.
After researching existing microcontrollers that support Bluetooth Mesh, we decided to go with the STM32WB55 series. STMicroelectronic provides a development kit P-NUCLEO-WB55. It consists of a Nucleo68 board and USB dongle device. See below:
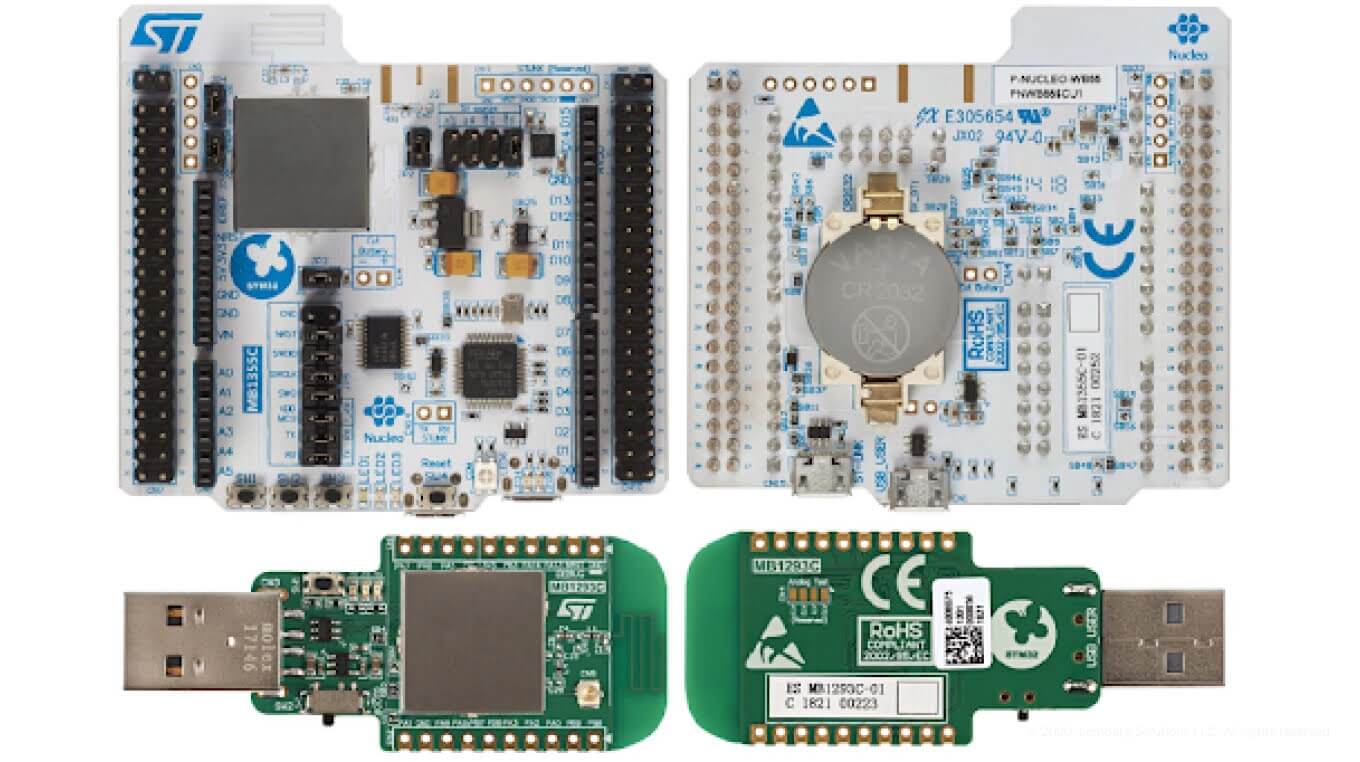
The STM32WB55 microcontroller is based on an Arm® Cortex®‐M4 core running at 64 MHz (application processor) and an Arm® Cortex®‐M0+ core at 32 MHz (network processor). It supports both Bluetooth™ 5.0 and Mesh 1.0 networking.
The STM32WB series is compatible with the STM32CubeMX MCU initialization, configuration, and code generation tool, as well as with STM32CubeMonRF software to test and validate RF performance.
The MQ-2 sensor was chosen as a smoke detector. This sensor is used in gas leak detection equipment for home and industry application. It can detect LPG, i-butane, propane, methane, alcohol, hydrogen and smoke. MQ-2 has a digital output that signals the current status. Detection threshold can be changed using the on-board potentiometer.

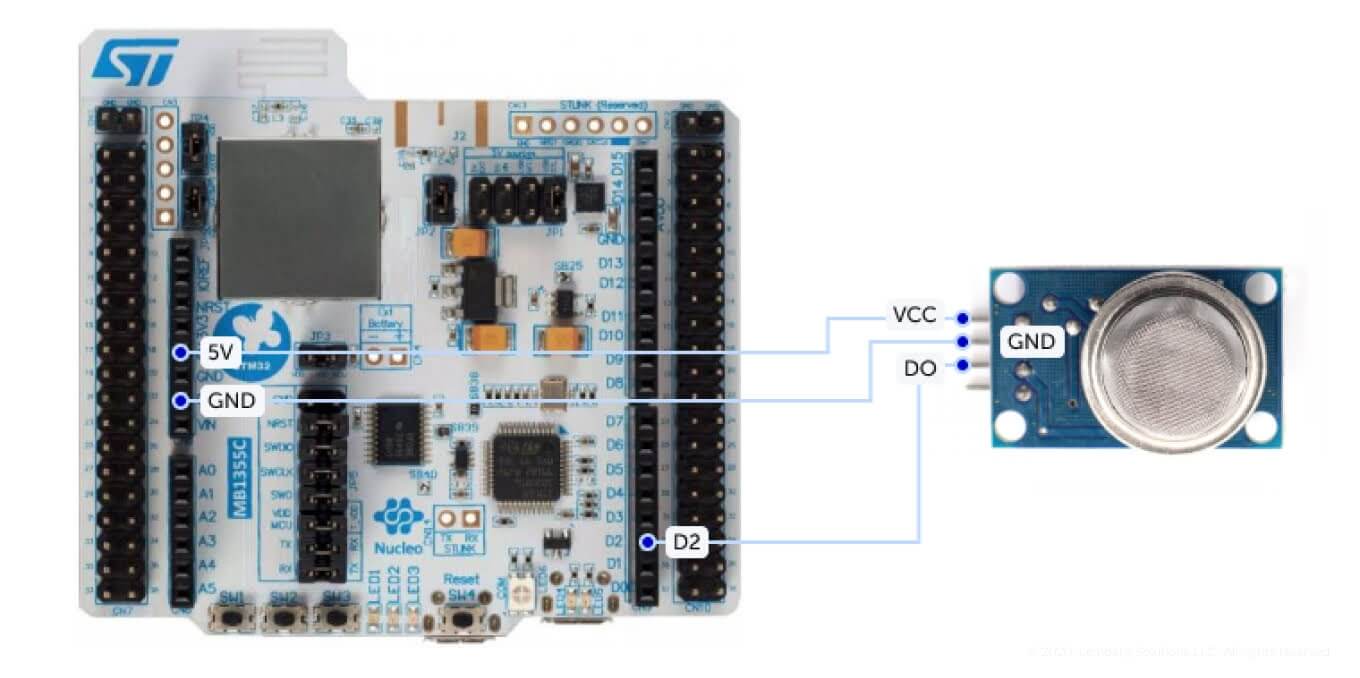
2. Smoke detector schematic
Pay attention to the schematic of the smoke detector. MQ-2 sensor input voltage and digital logic levels equal to 5 V. Due to that, DO output should be connected to a 5 V tolerant pin (D2 on the Arduino shield connector on the Nucleo68 board).
3. Node configurations
Each node runs the same firmware and is configured by a provisioner - in our case it’s a smartphone application. To transmit a sensor state, each node uses one client model. Other nodes can access the sensor state polling this model.
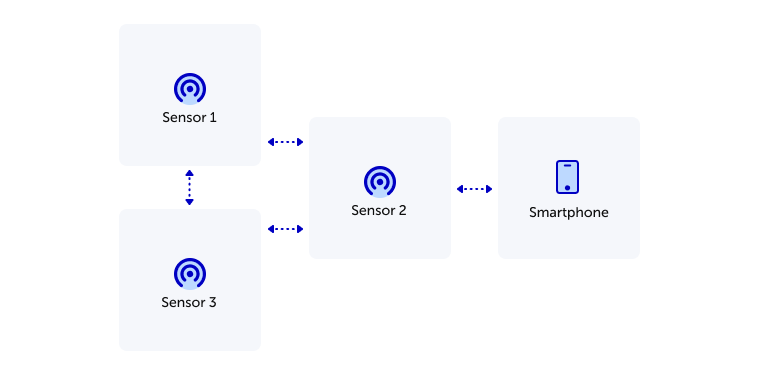
4. Network topology
After provisioning, all sensors get connected into a single Bluetooth Mesh network. Users can read data from sensors using a smartphone.
5. Test setup
For test setup, we created three sensors and provisioned into one Bluetooth Mesh network. Because of Bluetooth Mesh technology, users can connect to the network using a smartphone and monitor all node states even if only one node is located in the transmission area of a smartphone. During testing at least 10 m and one wall between each node were reached. In this case, the smartphone was able to communicate directly only with one node, but using Mesh it had access to other nodes too.
The mobile application makes it possible to monitor data from all sensors on the Mesh and configure the node features. See below the model of mobile application.
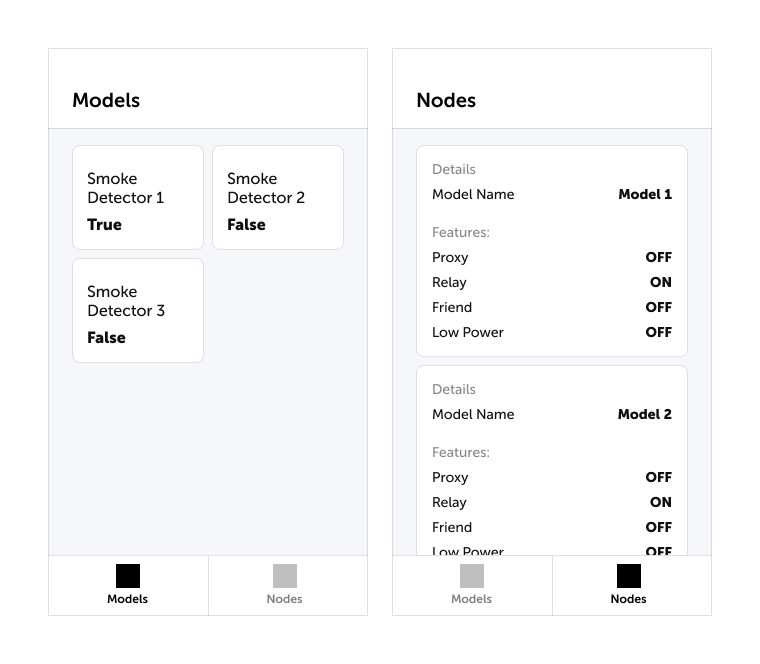
After taking all these steps, the general view of your node device should look like this one.
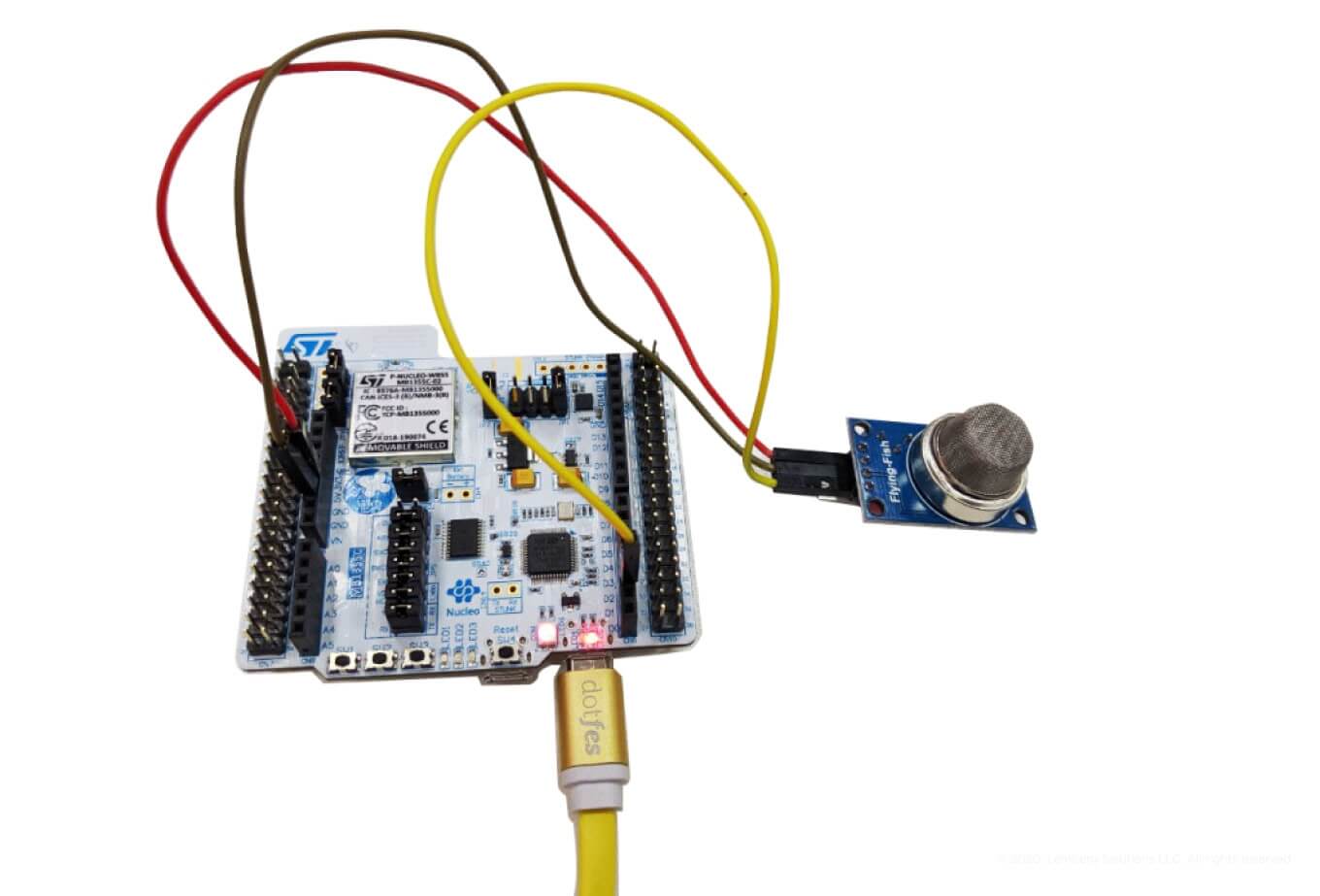
Our approach makes it possible to build a variety of sensor systems and integrate them into existing Bluetooth Mesh networks.
Reimagine your buildings with Lemberg Solutions
The addition of mesh networks brings to BLE devices an essential networking paradigm. The network size and scope can easily be extended with the use of Bluetooth Mesh technology.
This allows such companies as Lemberg Solutions to develop solutions that will breed results to your business. The demo we showed is one out of dozens applications of BLE mesh technology.
We are here to help you to reimagine the solutions of your smart buildings and to implement new ideas to your next use cases. Contact us for more information on how to implement IoT solutions at your business.