The Internet of Things has advanced the healthcare industry by innovating remote patient health monitoring using real-time data collection and processing. Now, healthcare facilities have the opportunity to react to abnormalities quickly and prevent disease deterioration.
However, the growth of healthcare IoT enabled hundreds of new cybersecurity threats and attacks for sensitive health data, making healthcare IoT security one of the crucial aspects of medical device development.
In this article, you'll discover the importance of IoT security for medical facilities, the most common IoT security threats in the healthcare sector, and actionable techniques to prevent IoT vulnerabilities in healthcare cybersecurity.
What is IoT security in healthcare?
IoT security in healthcare refers to integrating solutions and techniques into medical device development and maintenance to protect the confidentiality, integrity, and availability of healthcare information collected and transmitted between IoT devices within one network.
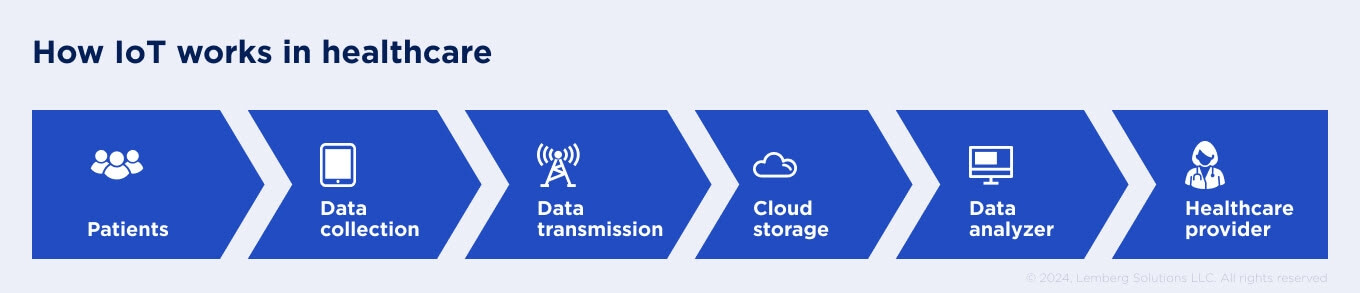
Security is paramount as medical IoT systems collect, transmit, and store sensitive patient health information. All industry regulations and compliance must be considered to protect patients' data and ensure a safe environment for data processing.
Further, we will learn about these data regulations and compliance, examine the role of security in healthcare IoT networks, outline the most widespread security vulnerabilities, and describe practical solutions to prevent them.
What role does security play in IoT medical devices?
IoT has significantly transformed the healthcare industry by introducing interconnected device networks that provide remote patient monitoring, health self-management, disease deterioration prevention, inventory, and medical equipment management.
Security has become a considerable challenge with the development of technologies, as over 90% of healthcare units that adopted IoT face cyberattacks. That is why healthcare facilities have challenges in using IoT and do not rush with its implementation, which impacts the whole healthcare IoT market.
Simply, they need to transparently see how the patient data will be used and processed and how they can protect it from breaches and attacks.
However, IoT security measures don't remain the same. The appearance of new cyber threats boosts healthcare IoT security development and enhancement.

5 most widespread IoT security threats in healthcare
According to the FBI report, over 53% of IoT medical devices are under critical security threats.
One of IoT medical devices' most anticipated security vulnerabilities is outdated software and hardware or unpatched and incompliant devices. As a result, these security threats may significantly impact patients' safety, PHI confidentiality, and healthcare units' operational processes.
We researched the most widespread medical IoT security threats. Let's find out what they are and what impact they may have on healthcare units and patients' safety.

1. Disclosure of patient health information (PHI)
The risk of disclosing or losing sensitive health information is the number one in healthcare IoT security.
Medical IoT networks usually unite hundreds of medical devices that collect and transmit information to a central system located in a healthcare unit. They process large volumes of data daily, and the vulnerability of data breaches is high as it is accessed by medical personnel and can easily be viewed or copied.
2. Legacy hardware
Using outdated hardware components for medical devices is another considerable security risk caused by the lack of regular updates on medical devices due to the high equipment cost. This requirement cannot be neglected, as regular medical solutions updates ensure secure communication within the IoT network.
Moreover, each medical device must comply with industry standards like HIPAA, FDA, MDR EU, and others to be used for medical purposes, so it is crucial to keep up to date with these regulations and their updates.
3. Unauthorized IoT network access
Unauthorized access to an IoT network can prevent data from reaching the endpoint and cause device or system breakdowns.
Only authorized parties and users can access data stored in IoT medical devices. It entails establishing an access security policy that includes requirements for passwords, ways of system authorization, access to different types of patient health information, availability of copying, and standards of data usage.
It should comply with your healthcare facility's requirements as well as with industry regulations that define how patient data can be collected, transmitted, stored, and used.
4. Wireless connectivity attacks
Many cyber attacks target data transmission from medical devices to a centralized system.
Despite widespread vulnerabilities, new threats keep developing and attacking IoT in healthcare due to the wireless connection. They primarily aim to disrupt the data transmission process, preventing patient data from reaching the endpoint.
It is crucial to integrate secure communication protocols to ensure an uninterrupted and protected data collection process. Nevertheless, we examined some of the IoT cybersecurity threats known in healthcare to be aware of.
- Selective-forwarding attack
The selective-forwarding attack is a security threat for wireless networks that harms data routing from sensors to the cloud and a central system, meaning healthcare providers. Here is how it works: malicious nodes selectively target data packets while this data is transmitted from devices to the next point.
This threat might have terrible consequences as it interrupts real-time remote patient monitoring. As a result, healthcare providers will not receive alerts of patient health abnormalities and emergencies on time, which can lead to disease deterioration or fatal cases.
- Sinkhole attack
Another way to steal sensitive patient data within the Internet of Medical Things network is a sinkhole attack. Its purpose is to pretend to be the most viable route for data from IoT devices to healthcare facilities.
Eventually, all PHI collected from sensors is transmitted to malicious storage, and healthcare providers don't receive all information or some piece of this information about patients.
Combined with a selective-forwarding attack, sinkhole one becomes even more powerful and dangerous, so it is crucial to be aware of this potential threat and consider it in security strategy.
- Jamming
The goal of the jamming attack is to interrupt wireless communication between IoT devices, be it Wi-Fi, cell network, or BLE. Eventually, sensors catch data but cannot transmit it to another network device.
The situation can even be worse if data is transmitted to several devices simultaneously to see the whole picture of patient health. It can impact one device connected to the network as well as the entire IoT device ecosystem.
5. Improper authorization of connected devices
The number of interconnected IoT devices within a specific healthcare unit may grow daily, whether a new device within the facility or a newly connected patient for remote monitoring. Violating the correct flow of configuring new devices or systems within an IoT network leads to improper operation, including the probability of unauthorized data access.
Proper setup and authorization of a new device are crucial to identifying this device across the network and protecting IoT system security.
Indeed, the list of security risks to medical IoT devices mentioned above is incomplete, as this number grows practically every day.
However, IoT security measures also keep up with these changes, and further, we will learn how exactly you can handle all of these risks.
How to protect your IoT medical devices: practical solutions
Despite the growing number of IoT security attacks, security measures to prevent these attacks are also being developed.

Further, we share practical tips and solutions for ensuring your healthcare IoT system security and maintaining it appropriately in all medical facility processes.
- Compliant medical device development
The first crucial step towards a secure IoT network is the development of industry-compliant medical devices that will be included in this network. Healthcare medical device development differs significantly from other domains by its strict data collection and transfer regulations, dividing devices into classes by types and applications, including safety.
That's why you should be responsible for choosing your software development vendor. Ensure the healthcare software development you work with has all the required certifications, compliance, and industry knowledge to complete the project. These include MDR EU, IEC 62304:2006, ISO 13485, HIPAA, GDPR, DiGa, and FDA.
- Establish a secure authentication policy
As mentioned above, improper setup of new devices within an IoT ecosystem leads to increased security threats of malicious network access and data breaches. That is why establishing a reliable security policy is essential, including configuring and authentifying new devices, data collection and transfer processes, granting access, and setting up passwords.
Strong passwords, multi-factor user and device authentications, and restricted access to a central system help protect your IoT network from cyberattacks and prevent sensitive data disclosure.
- Regular software and firmware updates
Medical software, such as a central data storage system, and firmware, such as software embedded into medical devices within your IoT network, require constant support and regular updates. This step is essential to maintaining a high-security level, preventing new cyber security threats, and overseeing vulnerabilities that may harm patient safety.
If the software system, connected to the network as an endpoint, can be updated per your request, firmware is more complicated. When developing firmware for your devices, OTA update functionality is a must. However, you can upgrade an existing firmware solution with new functionalities to ensure the highest sensitive data protection.
- IoT network segmentation
The number of interconnected devices within one IoT network is commonly unlimited. However, the more devices are connected, the more complex their security management becomes.
Segmentation is a practical solution that will simplify IoT medical device security monitoring, as all IoT medical devices will be split into different groups with different access to security controls, data encryption protocols, and authentication methods.
- Security audits
New security threats for IoT solutions appear practically every day, and it is essential to keep up with their development and take measures to remove them from your IoT network.
Regular security audits will simplify investigating new vulnerabilities, ensure secure data collecting, transmission, and storage, and review compliance with industry standards and regulations. Security audits can be set up as a regular activity for your IoT network in collaboration with your healthcare development partner.
- Staff training
To keep up with IoT security threats and be aware of how to detect and prevent them, you should consider staff training a vital part of your IoT medical system security. Depending on their position, medical workers access remote monitoring devices daily that collect sensitive patient data. All of them should know what cybersecurity threats exist, how to determine their types, and what measures they must take to prevent harm.
IoT medical device development with Lemberg Solutions
Over the past 15 years, we have succeeded in growing solid expertise in medical device development, as proven by international compliance and regulations such as ISO 13485, IEC 62304, HIPAA, DiGa, and MDR EU.
Medical device development requires a specific approach as it entails collecting, analyzing, and storing sensitive medical data. Deviations from the established industry regulations in the development processes cannot be tolerated.
Each type of medical software, whether healthcare management software, telemedicine platform, or virtual chatbot assistant, must be correctly classified depending on its purpose and impact on a patient's health and safety.
Gain more insights into medical software development and its specifics from our experience at the following link.

Summing up
Looking for a trusted healthcare software development partner might take time, but this step is crucial if you expect industry-compliant delivery. Whether you want to validate the feasibility of a medical device idea, build a solution from zero point, or improve the efficiency of an existing system, you have come to the right place.
Our team of experts provides end-to-end medical device development service, guaranteeing compatibility with industry regulations regarding data security and device quality as an ISO 13485-certified company.
Share your request for healthcare solution development with our experts so we can come up with a practical action plan.





