Hardly a week passes without hearing of some breach of data security. Companies big and small are affected by the actions of criminal enterprises seeking private information for their own ends. Such exposure of data is often enabled by poor security protocols or insufficient diligence by those tasked to protect it.
In such an environment of risks to personal information, it is necessary to adhere to the highest standards of protection. By addressing prospective threats in advance and making certain proper procedures are followed, customers can rest assured that their interests are upheld in a formal contractual manner.
Lemberg Solutions is fully compliant with the European Union’s General Data Protection Regulation (GDPR) and offers data processing agreements to ensure information security with clients and to protect their data. Learn all about them in this article by Lemberg Solutions CTO, Lyubomyr Dutko.
What is a data processing agreement?
A data processing agreement, or a DPA, is an agreement between a Data Controller (a client) and a Data Processor (a service provider such as Lemberg Solutions) which regulates the Data Processor’s access to the Data Controller’s data and the ways in which it can be processed for business purposes. Sometimes, DPAs are also referred to as GDPR data processing agreements.
In the simplest terms, by signing a data processing agreement with Lemberg Solutions, you know exactly who will have access to your data on our side and exactly how they are going to use it. So the central purpose of this document is role distribution.
It’s important to note what exactly is understood by data processing. It includes any operation in which data is collected, classified, communicated, or otherwise used to produce business value for the client.
READ ALSO: Lemberg Solutions Receives ISO 9001:2015 and ISO 27001:2013 Certifications
The “perfect flow” in a data processing agreement
When a customer submits a request for our services, the first step we take is to classify their data as to what type it is (e.g., medical information) in order to identify who will have access to it. We are able to convert the information into anonymized or “synthetic” data in order to limit the scope of individuals who will have actual access to the underlying raw information.
We next formulate who will develop the project’s information, such as the people in the development environment, in order to precisely determine the specific persons who will have access to the project’s private data. The result of this process is that the client will know at all times who will handle their important data.
Finally, we check the Technical and Organizational Manuals (TOMs), data categories, and the legal framework for your information. This leads to a solid understanding on both sides as to how your information will be treated while the project progresses.
The goal is to limit team access to real production data to 0. This is especially important when dealing with special types of data like healthcare information. Only a strictly limited group of people may have access to production to confirm that the delivered or deployed logic of potential hotfixes is applied and the system performs as expected.
We work with a capable third-party security firm, Iterasec, to ensure your data is protected. Our long-term contractual arrangement with Iterasec, led by their proficient representative Igor Kantor, means we have unbiased support for software mechanisms to prevent security incidents. Because they live in a culture of security, follow its certifications, and have access to the latest security news and practices, their absolute goal of ensuring your IS is integrated well into our own processes.
Additionally, Iterasec brings with it a great deal of expertise, with security teams, penetration testing, cloud security, threat modeling, security compliance consulting, and other competencies that enhance our culture of information security.
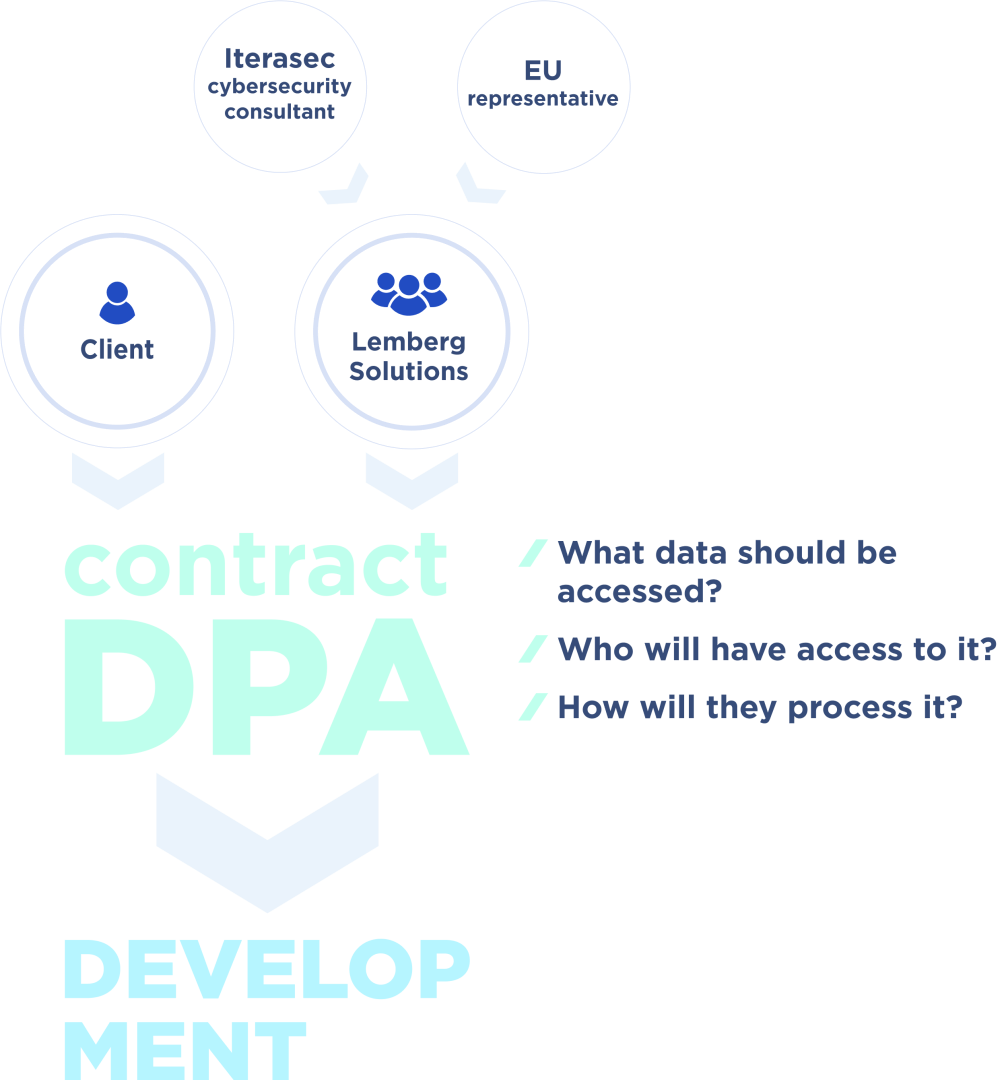
Once again, only the specific people mentioned in the data processing agreement will ever be in contact with your data — Lemberg Solutions knows that we are only the Data Processor for your information, while you are the Data Controller.
FAQ
- Does Lemberg Solutions have the infrastructure and know-how to carry out all of its commitments?
Yes, we do have the necessary infrastructure in place. One key aspect of this infrastructure is the Acceptable Use Policy we have developed together with Iterasec, which describes the acceptable use of and authorized access to Lemberg Solutions’ resources, including client data we interact with, and which each LS employee has to sign and adhere to.
Further, each of our team members follows our information classification policy and knows how to handle each piece of data they come in contact with depending on its label — public, internal use, or confidential.
We use only licensed software, powerful anti-malware solutions, Slack, which offers enterprise-grade data protection, as our main communication channel, and 1Password as our password manager.
All these measures combined allow us to provide our services on par or exceeding the best industry security standards. - What is the typical timeline for the data processing agreement process?
On average, it takes a week to bring together the various aspects (e.g., specialists, approvals, etc.). - What type of data must be indicated in the data processing agreement?
All types of data the client (Data Controller) intends to share with Lemberg Solutions (Data Processor) for further processing. - Is Lemberg Solutions fully compliant with all relevant security requirements?
Yes, through TUV Nord, a German Technical Inspection Association, Lemberg Solutions is certified and adheres to ISO 27001:2013 (Information Security Management Systems) and ISO 9001:2015 (Quality Management Systems). Additionally, we are preparing to get certified for the ISO 13485:2016 standard, which describes a comprehensive quality management system for the design and manufacturing of medical devices. - What is Lemberg Solutions’ procedure if you reveal a data breach?
According to GDPR’s reporting requirements in the event of a data breach, relevant authorities must be notified within 72 hours. Here’s what the procedure looks like on the inside:
If we suspect a data breach, we have 48 hours to make an internal investigation, confirm that the data breach has indeed occurred, check what data has been lost, leaked, or harmed, and notify our EU partner, a German auditing and accredited certification firm out of Hamburg, which meets the data protection requirements of the Federal Data Protection Act for cloud computing. The firm then has another 24 hours to clarify all the necessary details and notify the responsible EU data protection authority. - Are your official agreements up-to-date with your recent additions of EU-specific data protection efforts?
Yes, Lemberg Solutions has integrated all of its recent activities with its German partners into its wider contracts. In this way, the Master Agreements between companies are updated to include Standard Contractual Clauses (SCC) adopted by the European Commission with this latest information. Further, the SCC with individual Lemberg Solutions employees (those with a specific need to deal with clients’ information) have also been properly revised. - Has the war in Ukraine affected the operational capabilities of Lemberg Solutions?
The company has and will carry out its responsibilities with no loss of effectiveness with its customers. We control the security of all our equipment, cloud services, and sensitive data through special software. The challenges of the current situation notwithstanding, we are fully integrated into EU standards and our mission and services are not adversely affected by the geopolitical situation. We remain a vital and capable partner going forward — without limitations.
If you have any further questions regarding our information security policy, data processing agreements specifically, or the range of tech consulting and engineering services, embedded development services, IoT development services, AI & data science, we provide at Lemberg Solutions, do not hesitate to ask them through our contact form.



